About Me
I am a Ph.D. candidate in Computer Engineering at Worcester Polytechnic Institute (WPI) in the Vernam Lab, advised by Prof. Shahin Tajik (He is super cool!).
My research lies at the intersection of hardware security, FPGA-based sensing, and GPU-accelerated cryptography. I develop physical-layer security frameworks that detect hardware tampering, side-channel leakage, and power-distribution anomalies using embedded sensors and chiplet-level impedance characterization. My works includes FPGA-based physical side-channel attacks on secured ICs Chypnosis (Look at Advisories for AMD and MicroChip) and impedance attacks LeakyOhm, as well as Laser-assited Optical side-channel attacks and defense LaserEscape. Beyond the physical layer, I contribute to system-level security in projects like HyperDbg, a hypervisor-based debugger and dynamic introspection framework that supports low-level system instrumentation and analysis for security research.
In my recent research, I am particularly interested in how memory-hard cryptographic primitives and GPU-based hardware mechanisms can be leveraged to provide measurable guarantees of computational honesty and workload integrity in large-scale AI systems.
Before joining WPI, I received my M.S. and B.S. degrees in Telecommunication and Hardware Engineering, where I worked on embedded system design and FPGA-based side-channel evaluation.
🔬 Highlighted Projects
Chypnosis introduces a new class of side-channel attacks that exploit undervolting-induced static leakage to recover cryptographic secrets. It demonstrates that even static power variations in CMOS circuits can expose sensitive information when carefully modulated under fault conditions.
FPGA-based physical side-channel and impedance analysis framework for detecting secret-dependent signal leakage in power distribution networks. Demonstrates how impedance responses can be exploited to fingerprint chip activity and extract secret bits.
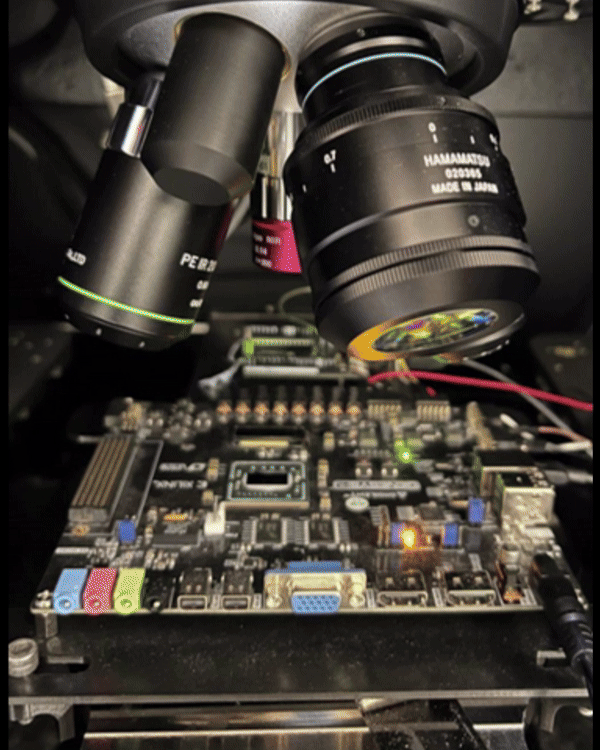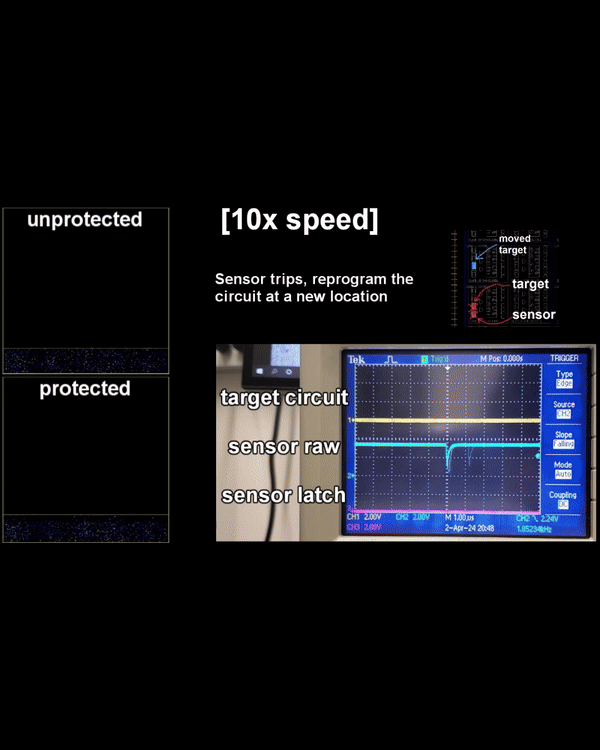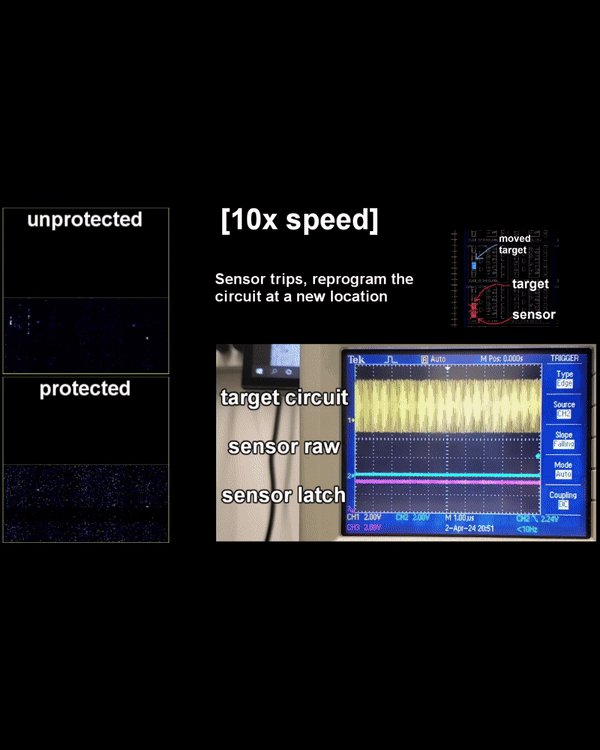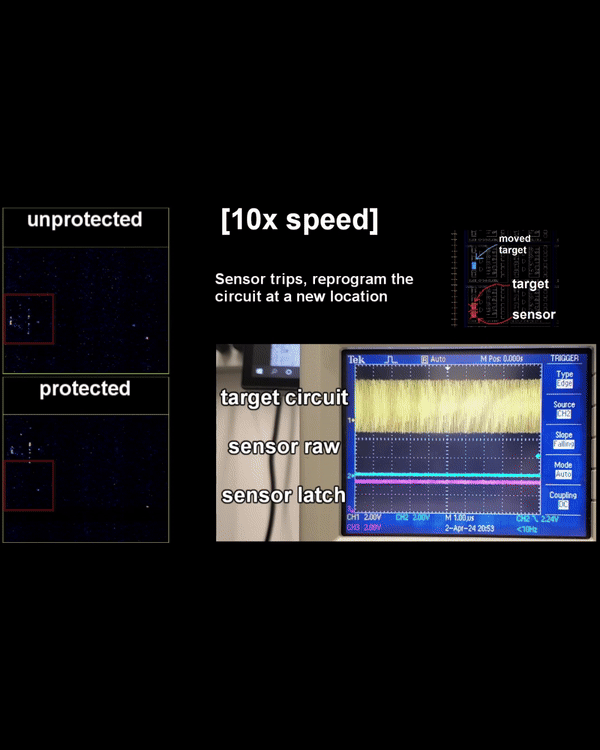
A laser-based side-channel and fault injection platform for exploring photonic leakage and fault resilience in cryptographic hardware. Provides sub-micrometer localization of leakage sources and enables optical countermeasure evaluation.
A hypervisor-based debugger and security introspection framework that enables dynamic kernel instrumentation, process tracing, and low-level system analysis. Designed for transparent debugging of OS internals and malware analysis on modern CPUs.
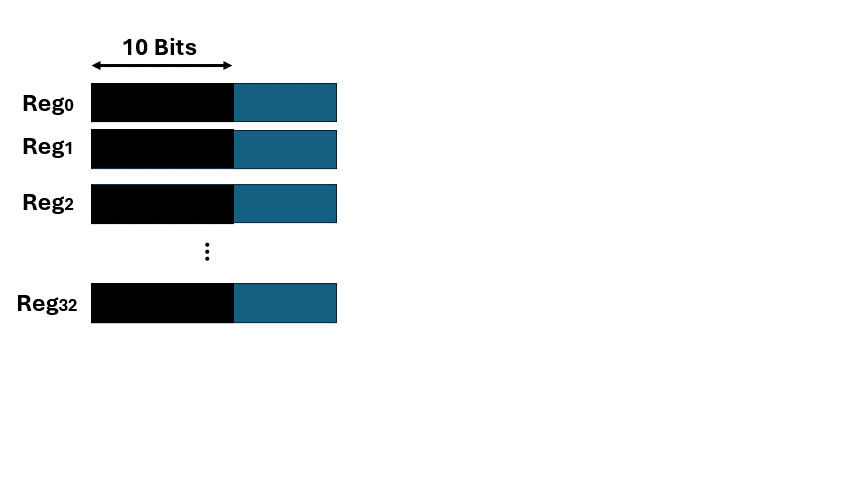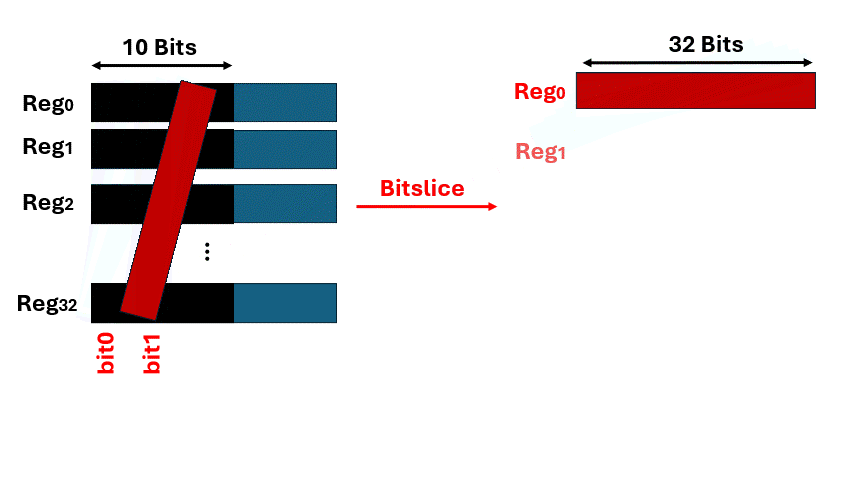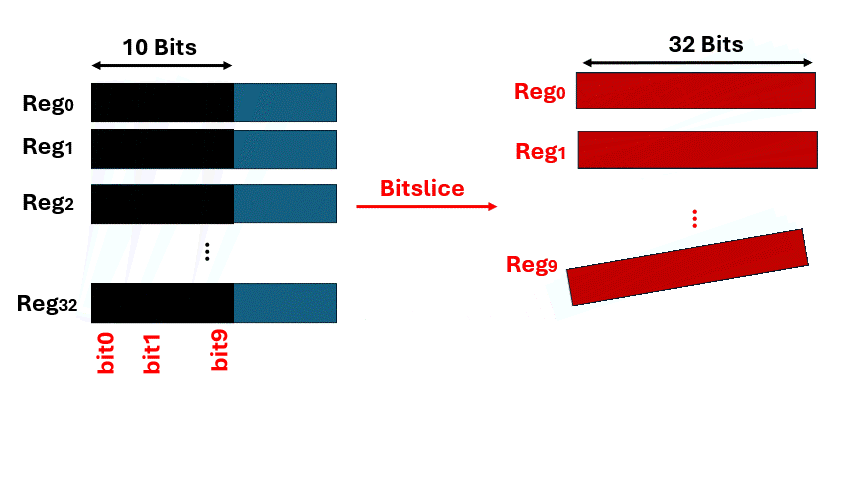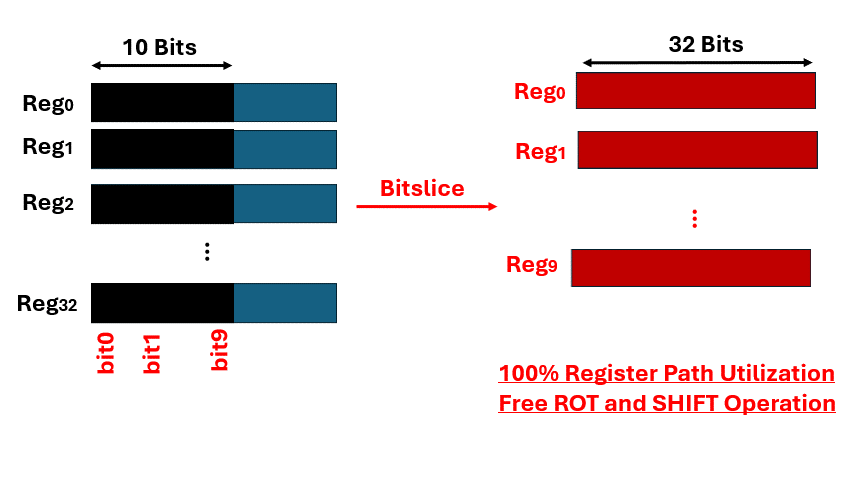
Bitslice layout enables massive parallelism by leveraging all SIMD/SIMT register paths simultaneously, removing data-dependent rotations and shifts inherent to traditional algorithms. The technique achieves 100% register utilization and constant-time execution, with the GPU-based AES implementation reaching up to 1.2 Tbps — one of the fastest known throughput records.```
📄 Highlight Publications
See more on Publications.
